中国网络安全、数据安全和个人信息保护法概览
中国网络安全、数据安全和个人信息保护法概览
I. Background
背景介绍
In recent years, the Chinese government has tightened the regulation of cybersecurity, data security, and personal information protection. Since 2016, three important laws (hereinafter referred to as the “Three Basic Laws”), namely, (i) the Cybersecurity Law of the People's Republic of China/《中华人民共和国网络安全法》 (“Cybersecurity Law”), (ii) the Data Security Law of the People's Republic of China/《中华人民共和国数据安全法》 (“Data Security Law”) and (iii) the Personal Information Protection Law of the People's Republic of China/《中华人民共和国个人信息保护法》 (“PIPL”) have been promulgated to lay down the foundation for the regulation in these areas.
近年来,中国政府加强了对网络安全、数据安全和个人信息保护的监管。自2016年以来,有三部重要的法律(以下简称 “三大基本法”),即:(i)《中华人民共和国网络安全法》(“《网安法》”),(ii) 《中华人民共和国数据安全法》(“《数安法》”)和 (iii) 《中华人民共和国个人信息保护法》(“《个保法》”)相继颁布,使相关领域的法律监管有据可循。
Government authorities, such as the Cyberspace Administration of China (“CAC”), have issued various regulations to implement the “Three Basic Laws”. In addition, other government and semi-government agencies, such as China’s National Information Security Standardization Technical Committee, have also released many national standards for more detailed guidance. More implementing regulations and national standards are being or yet to be drafted.
一些监管部门,例如国家互联网信息办公室(“国家网信办”),已经出台了系列法规及规范性文件来贯彻落实“三大基本法”。此外,其他政府监管部门和相关机构,如全国信息安全标准化技术委员会,也发布了许多国家标准以提供更详细的合规指引。与此同时,更多的实施细则和国家标准也在筹备中。
This article summarizes China’s current regulatory system of cybersecurity, data security and personal information protection based on the “Three Basic Laws”.
本文梳理了中国目前基于“三大基本法”而初步构建的网络安全、数据安全和个人信息保护监管体系。
II. Cybersecurity
网络安全
A. Jurisdiction of the Cybersecurity Law
《网安法》的适用范围与适用对象
The Cybersecurity Law applies to all network operators in China, including network owners, operators, and service providers. An entity that establishes and operates an internal network for its internal management purpose is also regarded as a network operator under the Cybersecurity Law.
根据《网安法》,在中华人民共和国境内建设、运营、维护和使用网络,以及网络安全的监督管理,都将适用网安法。即使运营者仅为了内部管理目的而建设、运营内部网络,也会被认定为属于受到《网安法》规制的“网络运营者”。
B. Multi-Level Protection Scheme (“MLPS”)
网络安全等级保护制度(“等保”)
Under the Cybersecurity Law, all network operators are required to fulfill the obligations under MLPS, including MLPS level determination and MLPS assessment.
根据《网安法》,所有网络运营者都需要按照等保制度的要求,履行安全保护义务,包括等保定级和评估。
1. MLPS Level Determination
等保定级
There are five levels under the MLPS. The higher the level, the stricter the required protection measures.
等保制度包含五个级别。级别越高,相应的保护措施要求就越严格。
a. Factors of MLPS Level Determination
等保定级的考量要素
In determining the MLPS level, the following factors will be considered:
在等保定级时,需考虑以下因素
(1)importance of the network system in national security and social and economic development; and
网络在国家安全、经济建设、社会生活中的重要程度;以及
(2)degree of damage that may be caused to national security, social and economic development, and legitimate rights and interests of other individuals or organizations in case of damage of the network system.
一旦网络系统遭到破坏后,对国家安全、社会秩序、公共利益以及相关公民、法人和其他组织的合法权益的危害程度。
b. Process of MLPS Level Determination
等保定级的流程
(1)A network operator is responsible to determine its own network system’s MLPS level.
网络运营者应当自行确定网络的安全保护等级。
(2)An operator of level-1 network systems does not need to file the level determination result to the public security authority for review.
一级网络系统的运营者不需要将定级结果提交公安部门审核。
(3)An operator of level-2 or higher-level network systems needs to: (i) organize experts to review the rationality of the determination; (ii) obtain the approval from the competent industry authority (if any); and (iii) file the result to the public security authority for review. If it fails the review, re-determination is needed.
对拟定为第二级以上的网络,其运营者应当(i)组织专家评审定级合理性;(ii)在评审后报请主管部门核准(如有);(iii)将结果报公安部门核准。如果核准不通过,需要重新认定。
2. MLPS Assessment
等保评估
a. The MLPS assessment is to assess whether a network operator’s protection measures can meet the requirements of the corresponding MLPS level.
等保评估的目的在于检验网络运营者的保护措施是否能够满足相应级别的保护要求。
b. Process of MLPS Assessment
等保评估的程序
(1)A network operator should engage an assessment service provider recognized by the government to conduct the assessment and issue an assessment report.
网络运营者应该聘请由政府部门授权的测评机构进行检测评估,并出具评估报告。
(2)An operator of level-2 or higher-level network systems is required to file such assessment report to the competent public security authority, which will issue a filing certificate if such report is approved.
二级或更高级别的网络系统运营者需要向相应的公安机关备案,并提交评估报告,如果该报告被核准,主管部门将颁发备案证书。
C. Protection of Critical Information Infrastructures (“CII”)
关键信息基础设施的安全保护
1. Definition of CII and CIIO
关键信息基础设施和关键信息基础设施运营者的定义
CII refers to key network facilities and information systems of key industries related to national security and public interest.
关键信息基础设施是指与国家安全和公共利益相关的、重点行业的重要网络设施和信息系统。
A CII operator (“CIIO”) is an entity that operates CII. A CIIO is required to implement special protection measures to protect its CII in accordance with applicable laws and regulations.
关键信息基础设施运营者是经营关键信息基础设施的实体。关键信息基础设施运营者需要根据适用的法律和法规实施特别保护措施,以保护其关键信息基础设施。
2. Identification and Protection of CII
关键信息基础设施的认定
Pursuant to the Regulations on the Security Protection of Critical Information Infrastructures/《关键信息基础设施安全保护条例》, governing authorities of key industries are responsible for formulating CII identification rules for their respective industries.
根据《关键信息基础设施安全保护条例》的要求,重点行业主管部门需结合本行业实际,制定本行业的关键信息基础设施认定规则。
Typical key industries include public communications and information service, energy, transportation, water conservancy, finance, public services, e-government, and national defense industries.
典型的重点行业包括公共通信服务、信息服务、能源、交通、水利、金融、公共服务、电子政务、国防科技工业等。
In practice, an entity that is identified as a CIIO may receive a specific notification from the authority. Once identified as a CIIO, the entity should implement more stringent security protection measures according to the applicable laws and regulations.
在实践中,被认定为关键信息基础设施运营者的实体可能会收到主管部门的通知。一旦被确定为关键信息基础设施运营者,该实体需根据相关法律法规实施更严格的安全保护措施。
III. Data Security
数据安全
A. Jurisdiction of the Data Security Law
数据安全法的适用范围与适用对象
The Data Security Law applies to all data processing activities conducted in China.
在中华人民共和国境内开展数据处理活动及其安全监管,适用《数安法》。
If data processing activities conducted outside China jeopardize (i) China's national security; (ii) China’s public interests, or (iii) the legitimate rights and interests of Chinese citizens or organizations, they will also be subject to the Data Security Law.
如果在中国境外进行的数据处理活动危及(i)中国的国家安全;(ii)中国的公共利益,或(iii)中国公民、组织的合法权益,也将适用《数安法》。
Under the Data Security Law, “data” includes not only electronic data, but also data recorded or stored in non-electronic forms (such as data recorded in paper files).
根据《数安法》,“数据”不仅包括电子数据,还包括以非电子形式记录或存储的数据(如纸质文件中记录的数据)。
B. Data Classified and Graded System
数据分类分级保护制度
The data classified and graded system requires relevant authorities to classify and grade data based on its importance and the degree of harm that will be caused by leakage or illegal use.
数据分类分级保护制度要求相关部门根据数据的重要程度以及发生泄漏或遭滥用后所造成的损害程度对其进行分级分类。
1. Governing authorities in charge of some sectors, such as industrial manufacturing, finance, and telecommunications, have already issued their data classification and grading guidelines for their respective sectors.
在工业制造、金融、电信等行业,相关行业主管部门已经发布了具有行业针对性的数据分类和分级指南。
2. In November 2021, CAC released the draft Administrative Regulations on Network Data Security (Draft for Comment)/《网络数据安全管理条例(征求意见稿)》 (“Administrative Regulations”) for public commenting, which divides data into three categories, namely (i) ordinary data, (ii) important data, and (iii) core data. However, the Administrative Regulations does not provide detailed data catalogues under these three categories.
2021年11月,国家网信办发布了《网络数据安全管理条例(征求意见稿)》(“《管理条例》”),向公众征求意见。《管理条例》将数据分为三类,即(i)一般数据,(ii)重要数据,以及(iii)核心数据。然而,《管理条例》并没有提供这三类数据的详细目录。
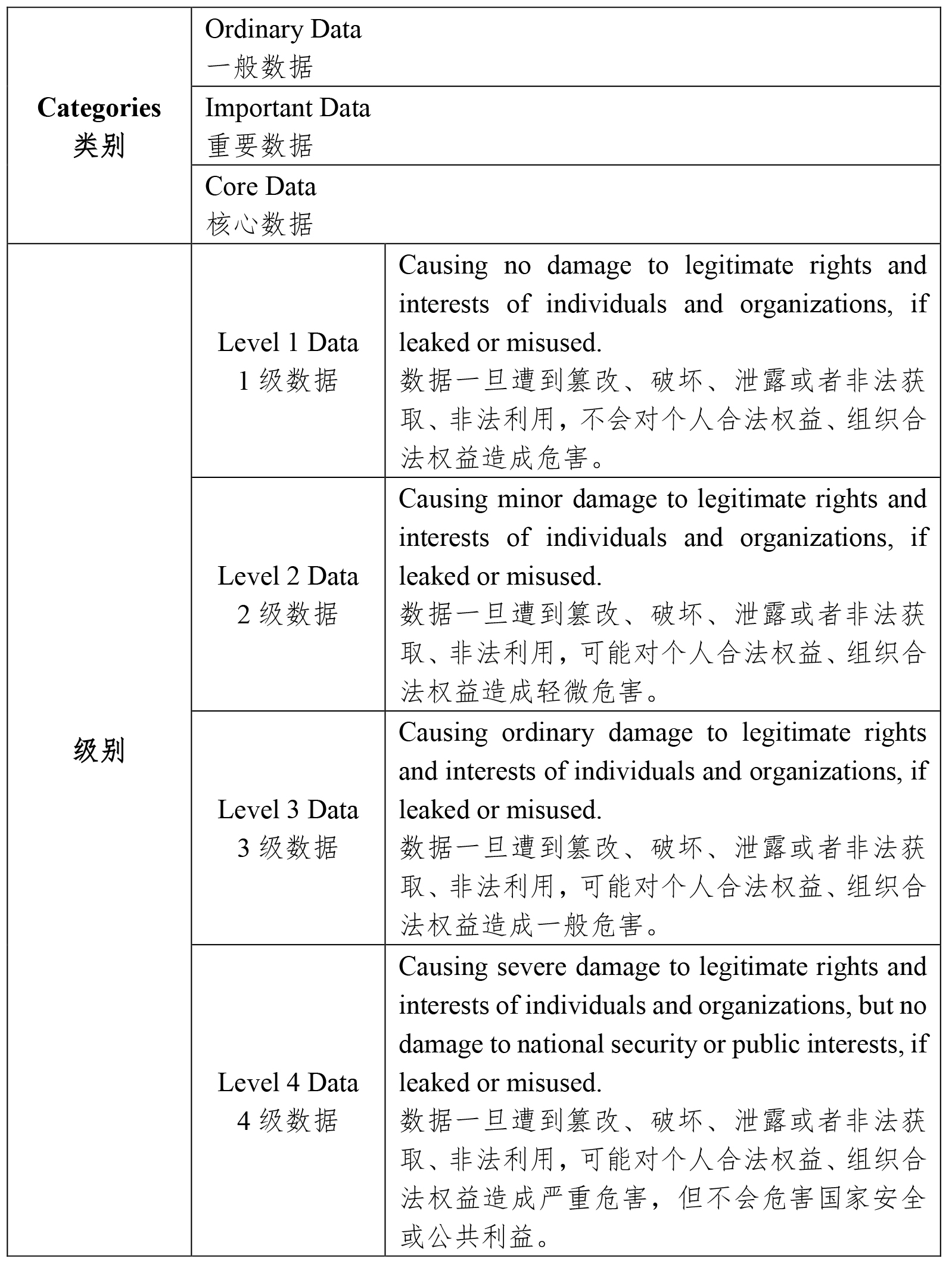
3. In December 2021, the Practice Guidelines for Cybersecurity Standards — Guidelines for Network Data Classification and Grading/《网络安全标准实践指南—网络数据分类分级指引》 (“Data Classification and Grading Guidelines”) was released, dividing data into three categories and four levels.
在2021年12月,《网络安全标准实践指南-网络数据分类分级指引》(“《数据分类分级指引》”)发布。《数据分类分级指引》将数据分为三个类别和四个等级。
点击可查看大图
4. There are inconsistencies between the Administrative Regulations and the Data Classification and Grading Guidelines. As of the date of this article, the Administrative Regulations is still a draft for public commenting and has not been officially adopted. The Data Classification and Grading Guidelines has already taken effect, but it is a recommended standard without mandatory power. It is still unclear what the final data classification and grading rules would be.
《管理条例》与《数据分类分级指引》的内容存在不一致之处。截至本文发布之日,《管理条例》仍是一个征求意见稿,尚未正式生效。《数据分类分级指引》业已生效,然而它是一个推荐性标准,并不具备法律强制力。因此,对于数据分类和分级规则的最终方案,我们尚无法得知。
C. Protection of Important Data
对重要数据的保护
1. Formulation of the Catalogue of Important Data
重要数据目录的制定
China’s central government is required by the Data Security Law to formulate a catalogue of important data based on the data classified and graded system, while relevant authorities in different regions and industries are then required to identify important data and formulate detailed implementing catalogues for their respective regions and industries.
《数安法》要求中央政府在数据分类分级制度的基础上制定重要数据目录,而各地区、各部门应当按照数据分类分级保护制度,确定本地区、本部门以及相关行业、领域的重要数据具体目录,对列入目录的数据进行重点保护。
2. Identification of Important Data
重要数据的识别
Both the Administrative Regulations and the Information Security Technology - Guidelines for Important Data Identification (Draft for Comments)/《信息安全技术 重要数据识别指南(征求意见稿)》 (“Guidelines for Important Data Identification”), a non-mandatory national standard issued by China’s National Information Security Standardization Technical Committee, provide rules for identifying important data.
《管理条例》和《信息安全技术重要数据识别指南(征求意见稿)》(“《重要数据识别指南》”)都为识别重要数据提供了指导规则。其中,《重要数据识别指南》是全国信息安全标准化技术委员会发布的非强制性的国家标准。
Important data refers to the data that may endanger national security or public interests once tampered, damaged, leaked, illegally obtained, or illegally utilized.
重要数据是指一旦遭到篡改、破坏、泄露或者非法获取、非法利用,可能危害国家安全、公共利益的数据。
Identification rules under the Administrative Regulations and the Guidelines for Important Data Identification are generally consistent with each other. However, although the Guidelines for Important Data Identification expressly excludes personal information from the scope of important data, the Administrative Regulations requires processors of personal information with an amount of more than 1 million people to take security measures equivalent to those of important data processors.
《管理条例》和《重要数据识别指南》中的识别规则大致相同。然而,《重要数据识别指南》明确将个人信息排除在重要数据的范围之外,但《管理条例》则要求处理一百万人以上个人信息的处理者需采取与重要数据处理者相同的安全措施。
3. Obligations of Important Data Processors
重要数据处理者的义务
A processor of important data needs to (i) designate a person in charge of data security; (ii) set up a security management department; (iii) conduct regular risk assessment for its processing activities, and (iv) report the assessment’s result to the relevant authority.
重要数据的处理者需要(i)明确数据安全负责人;(ii)明确数据安全管理机构;(iii)对其数据处理活动定期开展风险评估以及(iv)向有关主管部门报送风险评估报告。
According to the requirement of Cybersecurity Law, a CIIO should store important data in China. If it needs to transfer important data out of China, it needs to (i) go through security assessment organized by CAC; (ii) conduct by themselves or entrust cyber security service institutions to conduct the testing and assessment of their cybersecurity and potential risks at least once a year, and (iii) file such reports to the local cyberspace administration.
根据《网络安全法》的要求,关键信息基础设施运营者原则上应将重要数据存储在中国。如果需要将重要数据转移到境外,则需要(i)通过国家网信办组织的安全评估;(ii)自行或者委托网络安全服务机构对其网络的安全性和可能存在的风险每年至少进行一次检测评估,并(iii)将检测评估情况和改进措施报送相关负责关键信息基础设施安全保护工作的主管部门。
On July 7, 2022, CAC promulgated the Security Assessment Measures for Outbound Data Transfer/《数据出境安全评估办法》(“Security Assessment Measures”). The Security Assessment Measures requires not only CIIOs, but also other data processors to file for CAC’s security assessment before transferring important data out of China.
2022年7月7日,国家网信办发布了《数据出境安全评估办法》(“《安全评估办法》”)。《安全评估办法》要求除关键信息基础设施运营者之外的其他数据处理者在向境外传输重要数据前也应当向国家网信办申请进行安全评估。
D. Providing Data to Foreign Judicial or Law Enforcement Agencies
向境外司法机构或执法机构提供数据
If a processor needs to transfer its data out of China to a foreign judicial or law enforcement agency, it must obtain prior approval from the relevant authority before providing the data. However, as of the date of this article, relevant procedure to obtain such approval and the identity of “relevant authority” remains unknown. Also, what are deemed as “foreign judicial or law enforcement agencies” remain unclear.
如处理者需要将数据传输至境外司法或执法机构,其必须事先获得来自主管部门的批准。但是,截至本文发布之日,相关批准程序和“主管部门”的具体指代仍然不明。此外,关于“外国司法或者执法机构”的定义也尚未得到明确。
IV. Protection of Personal Information
个人信息保护
A. What is Personal Information?
什么是个人信息?
Under PIPL, “personal information” refers to all kinds of information related to an identified or identifiable natural person stored in both electronic and non-electronic form. Anonymized information will not be deemed as personal information.
根据《个保法》,个人信息是以电子或者其他方式记录的与已识别或者可识别的自然人有关的各种信息,不包括匿名化处理后的信息。
B. Jurisdiction of PIPL
个保法的适用范围与效力
1. PIPL is applicable to all personal information processing activities conducted in China.
《个保法》适用于在中国进行的所有个人信息处理活动。
2. PIPL also has extraterritorial jurisdiction. Processing activities conducted outside China will also be subject to PIPL, if:
《个保法》也有域外适用效力。在中国境外处理中国境内自然人个人信息的活动,有下列情形之一的,也适用本法:
a. the purpose of the processing is to provide products or services to natural persons in China;
以向境内自然人提供产品或者服务为目的;
b. the purpose of the processing is to analyze and evaluate the behavior of natural persons in China; or
分析、评估境内自然人的行为;或
c. other circumstances provided by laws and administrative regulations.
法律、行政法规规定的其他情形。
3. If an overseas entity is subject to PIPL, it needs to set up specialized agencies or designate representatives in China to handle personal information protection related matters and submit their names and contact information to relevant authorities. However, the detailed implementing rules have yet to be clarified.
境外的个人信息处理者,应当在中国境内设立专门机构或者指定代表,负责处理个人信息保护相关事务,并将有关机构的名称或者代表的姓名、联系方式报送履行个人信息保护职责的部门。该点的详细实施细则还有待立法者进一步明确。
C. Legal Basis for Processing Personal Information
个人信息处理的合法性依据
1. According to PIPL, a processor may process personal information on one of the following legal bases:
根据《个保法》,个人信息处理者可以根据以下依据之一来处理个人信息:
a. the individual's consent has been obtained;
取得个人的同意;
b. the personal information is necessary for the conclusion or performance of a contract to which the individual is a party, or for the implementation of human resource management pursuant to a lawfully concluded collective employment contract;
为订立、履行个人作为一方当事人的合同所必需,或者按照依法制定的劳动规章制度和依法签订的集体合同实施人力资源管理所必需;
c. the processing of personal information is necessary for the performance of statutory duties or obligations;
为履行法定职责或者法定义务所必需;
d. the processing of personal information is necessary for the response to a public health emergency, or to protect the life, health and property safety of natural persons in an emergency;
为应对突发公共卫生事件,或者紧急情况下为保护自然人的生命健康和财产安全所必需;
e. the processing of personal information is necessary for carrying out activities for public interests, such as news reporting and supervision by public opinion, and the processing is carried out within a reasonable scope;
为公共利益实施新闻报道、舆论监督等行为,在合理的范围内处理个人信息;
f. personal information that has been legally disclosed is processed within a reasonable scope in accordance with the PIPL; or
依照《个保法》规定在合理的范围内处理个人自行公开或者其他已经合法公开的个人信息;或
g. other circumstances provided by laws and regulations.
法律和法规规定的其他情况。
2. It is noteworthy that if the legal basis is individual’s consent, the processor should bear the burden of proof in the event of a dispute over the validity of the individual’s consent.
值得注意的是,如果是基于个人的同意而进行处理的,在对同意的有效性产生争议时,个人信息处理者应承担举证责任。
D. Principles for Processing Personal Information
处理个人信息的原则
1. Principle of Minimality and Necessity
最小必要原则
The scope of personal information’s collection and processing should be kept to the minimum extent that is necessary to achieve the purpose of processing. The processing activity’s impact on the individuals’ legitimate rights and interests should also be minimized.
个人信息的收集和处理范围应控制在实现处理目的所必需的最小范围。 处理行为对个人合法权益的影响也应被控制在最小范围内。
2. Principle of Openness and Transparency
公开透明原则
The personal information processor should clearly disclose to the individuals of (i) the scope of personal information to be collected, (ii) rules and purpose of the processing activity, (iii) name and contact information of the processor, and (iv) the ways for individuals to exercise their statutory rights under PIPL.
个人信息处理者应向个人明确披露:(i)收集个人信息的范围,(ii)处理活动的规则和目的,(iii)处理者的名称和联系方式,以及(iv)个人行使《个保法》项下权利的行权方式。
E. Deletion of Personal Information
个人信息的删除
1. Under any of the following circumstances, a processor should delete an individual’s personal information. If the processor does not delete the personal information, the individual has the right to request deletion.
有下列情形之一的,个人信息处理者应当主动删除个人信息。个人信息处理者未删除的,个人有权请求删除。
a. the purpose of processing personal information has been achieved, cannot be achieved, or the processing activity is no longer necessary for achieving the purpose;
处理目的已实现、无法实现或者为实现处理目的不再必要;
b. the personal information processors stop providing products or services, or the storage period has expired.;
个人信息处理者停止提供产品或者服务,或者保存期限已届满;
c. the individual withdraws his/her consent;
个人撤回同意;
d. the processing activity by the processor violates the laws, administrative regulations or the agreement; or
个人信息处理者违反法律、行政法规或者违反约定处理个人信息;
e. the individual exercises his/her rights to request deletion.
个人行使其权利要求个人信息被删除。
2. If laws and regulations require the continuous storage of personal information, the processor should take measures to ensure that such personal information will not be used for any purpose other than storage.
如果法律和法规要求长期存储个人信息,处理者应采取相应措施,确保这些个人信息不会被用于存储以外的任何目的。
F. Outbound Transfer of Personal Information
个人信息的跨境传输
1. Requirements of Outbound Transfer
跨境传输的要求
a. The processor should inform individuals of (i) the name and contact information of the receiver; (ii) the receiver’s processing method and purpose; (iii) the type of personal information to be transferred, and (iv) the ways for the individuals to exercise their relevant rights against the receiver, and the processor should also obtain the individuals’ separate consent.
处理者应告知个人(i)接收方的名称或者姓名和联系方式;(ii)接收方的处理方法和目的;(iii)将要传输的个人信息的类型,以及(iv)个人向接收方行使权利的方式。除此之外,处理者应当依照《个保法》规定取得个人的单独同意。
b. The processor also needs to conduct personal information protection impact assessment (“PIPIA”) for such outbound transfer.
处理者需要对该等跨境传输进行个人信息保护影响评估。
c. If the processor is a CIIO, it should pass the security assessment organized by CAC in advance.
如果处理者是关键信息基础设施运营者,它应该事先通过国家网信办组织的安全评估。
d. If the processor is not a CIIO, depending on the volume and nature of the personal information to be transferred, the CAC’s security assessment may or may not be required. More specifically, according to the Security Assessment Measures, if a non-CIIO processor processes personal information of more than 1 million individuals, or has transferred personal information of 100,000 people or sensitive personal information of 10,000 people overseas since January 1 of the previous year, it should file for CAC’s security assessment before transferring personal information out of China.
如果处理者不是关键信息基础设施运营者,根据其需要转移的个人信息的数量和性质,有可能需要通过国家网信办的安全评估。具体来说,根据《安全评估办法》的规定,如果处理者并非关键信息基础设施运营者,且(i)处理一百万人以上的个人信息或(ii)自上年1月1日起累计向境外提供10万人个人信息或者1万人敏感个人信息的,应当在向境外传输个人信息前向国家网信办申请进行安全评估。
e. If the processor is not a CIIO and CAC’s security assessment does not apply, it should meet one of the following requirements: (i) obtaining personal information protection certification issued by a professional organization; (ii) entering into a standard data protection contract with the receiver in accordance with CAC’s standard contract template; or (iii) satisfying other requirements stipulated by laws and regulations or CAC.
如果处理者不是关键信息基础设施运营者,且无需接受国家网信办的安全评估,则应满足以下要求之一:(i) 获得专业机构颁发的个人信息保护认证;(ii) 按照国家网信办的标准合同模板与接收方签订标准的数据保护合同;或(iii) 满足法律、行政法规或者国家网信部门规定的其他要求。
2. On June 24, 2022, China’s National Information Security Standardization Technical Committee issued the Practice Guidelines for Cybersecurity Standards — Security Certification Specifications for Cross-border Processing of Personal Information/《网络安全标准实践指南—个人信息跨境处理活动安全认证规范》(“Security Certification Specifications”). This document serves as guidance to how personal information security certification should be conducted for cross-border transfer of personal information. However, the Security Certification Specifications is only a recommended guideline without mandatory power.
2022年6月24日,全国信息安全标准化技术委员会发布了《网络安全标准实践指南—个人信息跨境处理活动安全认证规范》(“《安全认证规范》”)。该文件为如何针对个人信息跨境传输进行个人信息安全认证提供了指引。但《安全认证规范》仅为推荐性的指南文件,并不具有强制力。
3. On June 30, 2022, CAC issued the Provisions on Standard Contract for Outbound Transfer of Personal Information (Draft for Comment)/《个人信息出境标准合同规定(征求意见稿)》 (“Standard Contract Provisions”)and the standard contract template for the cross-border transfer of personal information. However, both the Standard Contract Provisions and the standard contract template are only drafts for comments and have not been officially adopted.
2022年6月30日,国家网信办发布了《个人信息出境标准合同规定(征求意见稿)》(“《标准合同规定》”)以及标准合同模板。但是,《标准合同规定》以及标准合同模板目前均为征求意见稿,尚未正式实施。
G. Individuals’ Rights
个人的权利
Individuals have the following rights:
个人在个人信息处理活动中享有以下权利:
1. The right of access and replication. Individuals have the right to access and replicate the personal information collected by processors.
查阅和复制的权利。个人有权向个人信息处理者查阅、复制其个人信息。
2. The right of portability. Individuals have the right to request their processors to transfer their personal information to other processors, if the conditions prescribed by CAC are met.
可携权。个人请求将个人信息转移至其指定的个人信息处理者,符合国家网信办规定条件的,个人信息处理者应当提供转移的途径。
3. The right of correction and supplementation. Individuals have the right to correct or supplement their inaccurate or incomplete personal information.
更正和补充的权利。个人发现其个人信息不准确或者不完整的,有权请求个人信息处理者更正、补充。
4. The right of deletion. Individuals have the right to request processors to delete their personal information, if the conditions prescribed by laws and regulations are met.
请求删除的权利。如果满足法律规定的条件,个人有权要求处理者删除其个人信息。
5. The right of withdrawal of consent. If the legal basis of processing personal information is the consent from individuals, individuals have the right to withdraw the consent to the processing of their personal information. The processor should provide convenient means to withdraw consent.
撤回同意的权利。基于个人同意处理个人信息的,个人有权撤回其同意。个人信息处理者应当提供便捷的撤回同意的方式。
6. The right for an explanation. Individuals have the right to request their processors to explain the rules for processing their personal information.
要求解释的权利。个人有权要求个人信息处理者对其个人信息处理规则进行解释说明。
V. Our Outlook
我们的展望
China's regulatory system of cybersecurity, data security, and personal information protection is still in the process of dynamic development, and many implementation issues have yet to be clarified. According to Protocol, a US tech media, in the last several months, CAC on average issued 40 notices each month.[1]
中国的网络安全、数据安全和个人信息保护的监管体系仍处于高速发展的过程中,众多问题仍亟待解决。据美国科技媒体Protocol报道,在过去的几个月里,国家网信办平均每个月发出40份官方通知。[2]
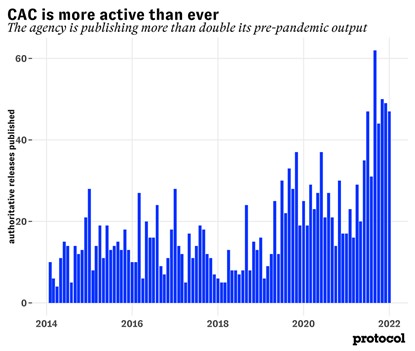
《国家网信办比以往任何时候都要活跃——该部门这两年来发布的文件数量是疫情前的两倍以上》
More regulations, national standards and notices may be issued in 2022 and going forward. To be well prepared for the challenges brought about by the uncertainties down the road, network operators and data processors should pay close attention to legislative developments and seek professional advice when necessary.
在2022年及今后的一段时期,预计将会有更多的专项法规、国家标准和规范性文件陆续出台。为了能够充分准备,以应对不确定性带来的诸多挑战,网络运营者和数据处理者应密切关注国内立法动态,必要时向专业人士寻求法律意见。
[Note]










